How and why hackers target small groups on social media
Lower your trust settings to beat the bots
One thing that constantly puzzles people about social media is the presence of bots. Not just the sexbots with obviously made-last-week profiles and thirst trap profile pics and posts; but the bots who seem to have thousands of (real) followers and have been on the platform literally for years. When you inspect their old postings, you often find that they only became bot-like at some particular point, and that if you go back far enough then you discover that they seemed to be quite normal people who didn’t rant about things.
In that respect, it can sometimes be a little tricky to discern the bots from someone who has just been radicalised by being Too Online. But there’s a particular process which the hackers who want to expand their bot networks use in order to grab existing accounts and monetise them twice over.
It’s-a not me, Mario
The tennis journalism beat is a pretty small one in real life, because despite all the money washing around the sport there’s never been gigantic interest from news organisations in what happens on the year-round circuit. It’s not like football (soccer or American) or basketball or cricket teams, where there’s always some intra-club intrigue—players/coaches/managers getting promoted/sacked; tennis tends to be a little quieter, even if the occasional coach/player topic does blow up and grab people’s attention.
On the social networks, there’s more latitude to be an observer/commentator/journalist, and of course people will tend to gravitate towards the people who are also writing or commentating on the same topic. And so they follow each other, often mutually, because it is The Way Of The Internet that one has to be constantly both looking over one’s shoulder for people coming up behind, and looking over the shoulder of anyone in front to see what they’re writing. (Don’t ask me how this metaphor works in the physical world. It’s a metaphor, don’t overthink it.)
This leads naturally to tightly coupled groups around a topic. Person A follows person B and C, who mutually follow them back, even on asymmetrical networks such as Twitter (now X). And the longer that tightly coupled group exists, the more its members trust each other.
Enter hacker-man. (Perhaps hacker-woman, but they’re much less common.)
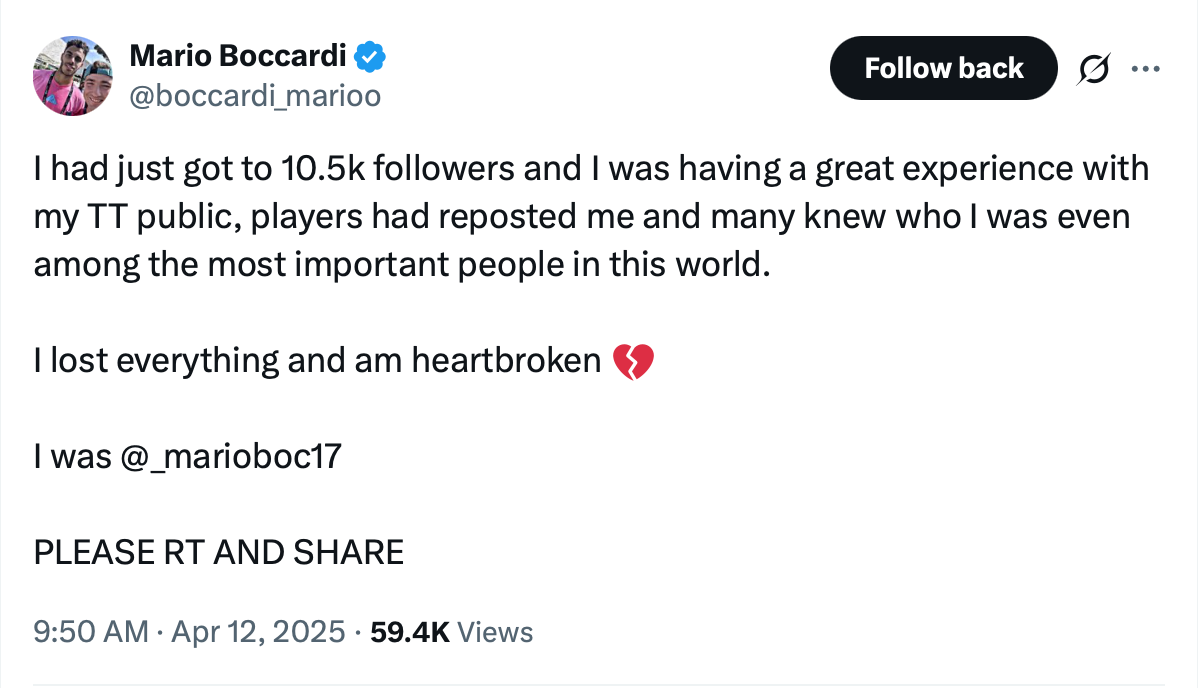
On April 12, Mario Boccardi, a young(er than me, which isn’t saying a lot, but he is) Italian tennis journalist, realised that he’d made a really bad decision when he’d clicked on a link in a direct message he’d received from an account that he knew.
The message said
“Hi, my account was hacked. And it’s worse, you’re involved too, and I reported your account by mistake. Follow [link] and they can fix it.”
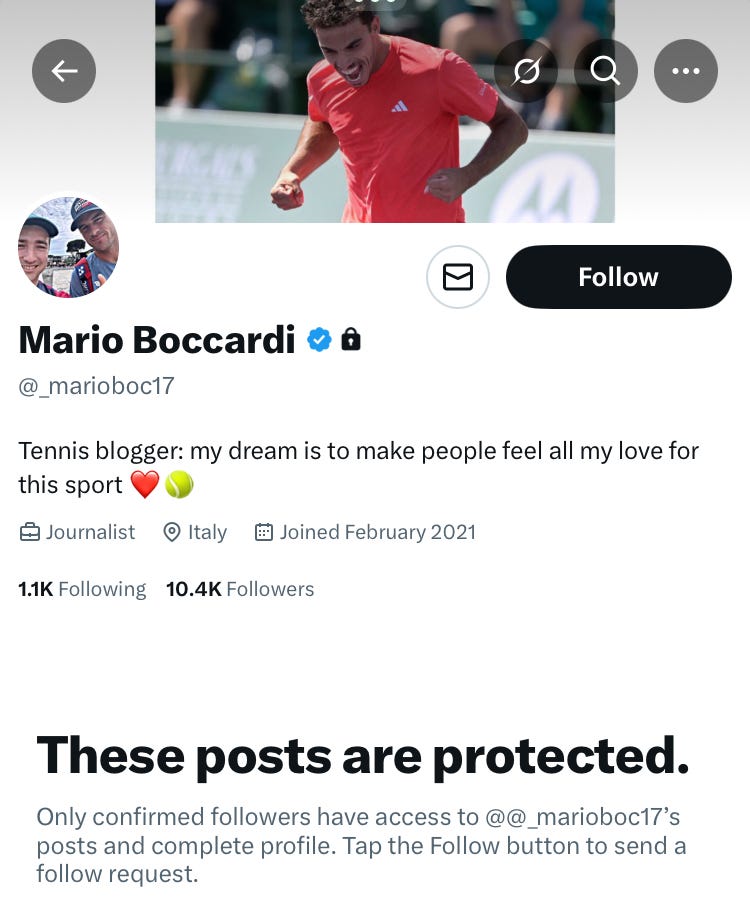
But the link led to a page which demanded his password, and just like that, his account was taken over. The hacker changed the phone number and email associated with the account, and set its posts to “protected”, so that only people already following the account could see what was being posted.
The effect on Boccardi, who quickly set up a new account while he contacted Support in the hope of some help, was unsurprisingly hard.
The ramifications of what had happened started to sink in.
But wait, you think: surely X Support can sort this out?
To which one replies: haha, who are you kidding? Helpful support is an oxymoron in these days of gigantic platforms, especially platforms which have slashed their support staff to the bone. The responses from X Support said, well, the email and phone number you’re giving us don’t match the number associated with the account.
The banging of heads against walls should be audible from here. So many people go through this experience, and yet there isn’t an algorithmic check at Support which asks 1) has the email and/or phone number associated with this account changed very recently? 2) has the account recently changed to “protected” status? You could add a third: is the request for support/account recovery coming from an email/phone number that was recently associated with the account? Given those, you could probably mop up and restore the majority of account thefts. All it would take is four extra columns in the user’s database table—PREV_ASSOC_EMAIL, PAE_CHANGE_DATE, PREV_ASSOC_PHONE and PAP_CHANGE_DATE—and you’d be able to sort these problems out. (Often the hackers also turn on two-factor authentication for the account—the lack of it being what enabled the hack in the first place—which should be another flag in the support database.
Because how often, from the platform’s point of view, do the following events happen:
an account changes its associated phone number and email
that account switches to protected mode
the account turns on two-factor authentication (2 and 3 are interchangeable in time order)
someone contacts Support saying that that account belongs to them and has been hacked, and their complaint comes from an email that was until very recently associated with the account
I can’t honestly think of an innocent explanation for that sequence of events. Sure, if you got a new phone and new phone number, and you were being tormented and worried about being hacked, then you’d do all of the first three. But No.4? How does someone send an email from the previous email associated with the account? A hacker wouldn’t have any simple avenue to know what it was, and would anyway have to spoof it. (Your problems multiply if your email is ever hacked, by the way. Turn on two-factor authentication! Get a code generation app such as Authy, or the Microsoft or Google ones, or let Apple’s generator do it.)
So here’s where Mario was left: locked out of his own account, whose posts he couldn’t even view because his new account hadn’t been following it (logically).
Stage 1 over, the hacker moved on to the next step: exploit the tight-knit nature of the group. Mario’s old account had more than 10,000 followers; his new one, at that time, had a handful. (I had added him to my tennis list—it’s how I separate topics out.)
DROP_TABLES the other shoe
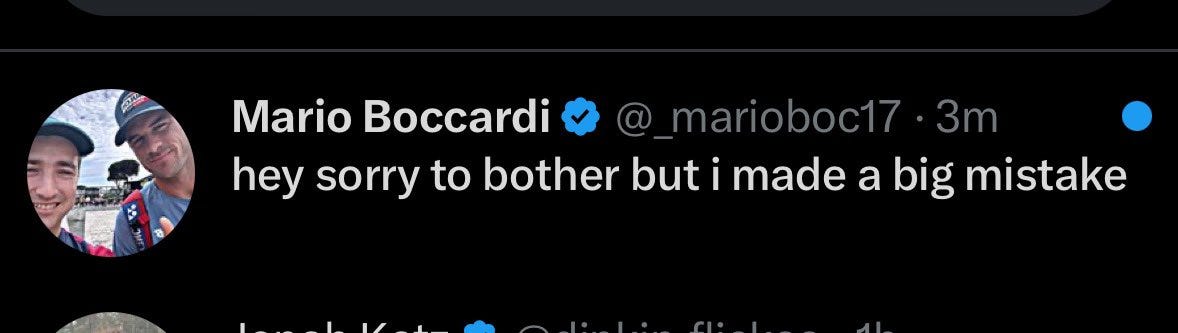
And how do you exploit a tight-knit group? By using exactly the same tactics that worked in the first place—exploit their trust of your account, and hoping they haven’t heard the news that you’ve taken it over.
Which meant a number of that ten thousand followers got a Direct Message:
Yes, it’s that “I got hacked and then reported your account but you can fix it at this link” phish. Some people will have got it and clicked on it; that’s how mistaken trust works. It’s how phishing works. It’s why you need TARS, the intelligent machine, to be less trusting than you when you noodle down to a distant planet to see how a scientist trying to save humanity is getting on1.
But we’re not finished yet! Although the hacker now has an account which has lots of followers, gained organically, which can be used for bot output (in the course of time, by unprotecting its tweets when the Sauron eye of Support has passed—I mean who are we kidding, it was never on it), that’s not enough. There’s money to be made by other means.
Stage 3: separation (from money)
As soon as Boccardi mentioned that he’d been hacked, I cringed a little, because something inevitably happens when anyone uses the words “account” and “hack” in the same post:
No, try my solution!
Pick me! Pick me!
Note the two-stage element in the first two replies: hacked accounts responding immediately with the name of a different person who will “help” you. (Also, that first one hasn’t been updated for the modern age, which means it’s been running for at least two years in that format. You can try reporting it: nothing happens. The account itself is a mixture of frenzied replies to hacked account despair or thirst trap sexbot pics.
The scam here is that if you get in touch with these “hackers”, they’ll tell you that sure, they can get it back for you. It’ll, uh, cost a little because they have to a) get in touch with their friend on the inside or b) use their extra-special hacking t00lz to get your account back.
You send over the money, and that’s the last you’ll ever hear from them. And so heads they win—they’ve got a hacked account that can be used for bot earnings and sexbottery—and tails you lose: you can’t get your account back.
And all because of the trust that emanates from being part of an enjoyable social group, using social media in a positive way, to associate with people who you like to hear from and whose views you find interesting and engaging. These are the groups that are most vulnerable to hacking: once a single account has been compromised, the others can fall like dominoes.
These are the accounts that any platform’s support system should try to identify and help out, rather than ignoring them and cutting them loose, as happened to Boccardi. (Who, good news, is gaining followers daily on his new account—follow him for fun Italian takes in English about tennis.) The fact that X support in particular doesn’t take a little care about this is indicative of how uninterested platforms are in their users beyond being eyeballs to project adverts onto. If your account does get hacked (because you didn’t turn on 2FA—turn it on! It’ll be there in the settings somewhere), then you’d better hope that you have an inside track to the people who run it, because otherwise you’re stuffed.
And yes, that can be annoying and heartbreaking in equal measure to discover how little the platforms care. Though the one benefit from the tight-knit groups can be how quickly they’ll try to pull people back up. Humans tend to be good. It’s just that their trust settings are too high.
• You can buy Social Warming in paperback, hardback or ebook via One World Publications, or order it through your friendly local bookstore. Or listen to me read it on Audible.
You could also sign up for The Overspill, a daily list of links with short extracts and brief commentary on things I find interesting in tech, science, medicine, politics and any other topic that takes my fancy.
• I’m away for a week. But please leave a comment here, or in the Substack chat, or Substack Notes, or write it in a letter and put it in a bottle so that The Police write a song about it after it falls through a wormhole and goes back in time, helped—no doubt—by TARS.
Interstellar sidebar, with spoilers: really, isn’t TARS the hero of the whole film? On the Water planet it saves Anne Hathaway, and hence the person who’s going to—I suppose?—keep humanity going in the far reaches of space. (I do question how those fertilised eggs or whatever are going to be grown into full humans. Like, whose womb, whether natural or artificial? When they’re born, they’ll be fed on what?) On the Ice Planet, it stops the space station being stolen, even if it can’t stop it being damaged. It takes over the controls to dock with the space station. It goes into the tesseract and takes the readings and gives them to Cooper so he can send them back to Murph who saves the day. Without TARS: no Anne Hathaway, no space station and hence no black hole readings and no future for humans. (Interesting question: how old is Murph when Cooper enters the tesseract? Given that little time seems to pass once he exits the tesseract, he must be much the same age through all of that passage—which means, doesn’t it, that Murph is already old when he enters the tesseract, but he’s able to interact with her reality at a different time; which is implied by his being able to move between different time locations in the tesseract.)






“quite normal people who didn’t rant about things.”
An oxymoron if there ever was one